XYCTF2024 Writeup By Flooc
XYCTF
re
你是真的大学生吗?
8086芯片的汇编,主要逻辑是将flag的一位与下一位异或,顺序为正序然后与上面的数据比较。
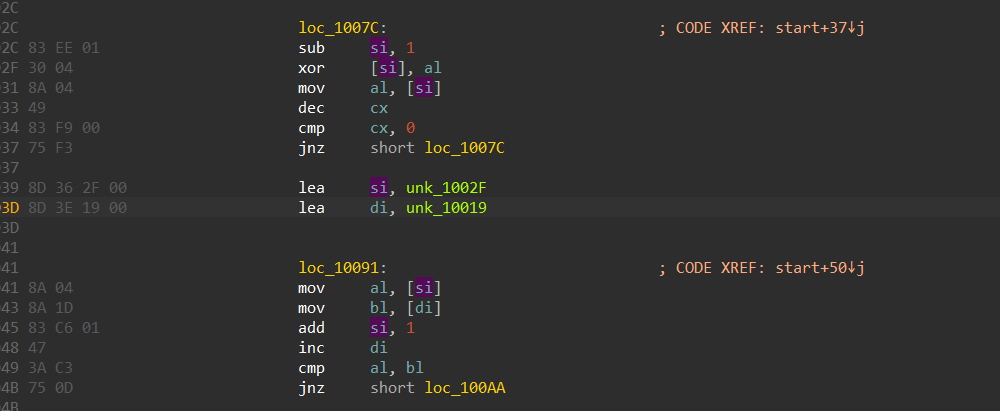
1 | table = [0x76, 0x0E, 0x77, 0x14, 0x60, 0x06, 0x7D, 0x04, 0x6B, 0x1E, |
1 | xyctf{you_know_8086 |
聪明的信使
1 | table = 'oujp{H0d_TwXf_Lahyc0_14_e3ah_Rvy0ac@wc!}' |
flag{Y0u_KnOw_Crypt0_14_v3ry_Imp0rt@nt!}
喵喵喵的flag碎了一地
拼flag
1 | flag{My_fl@g_h4s_br0ken_4parT_Bu7_Y0u_c@n_f1x_1t} |
DebugMe
本题只要apk在调试状态下即可getflag
使用jadx+雷神模拟器,可以直接调试,进入调试界面点击click me,出flag
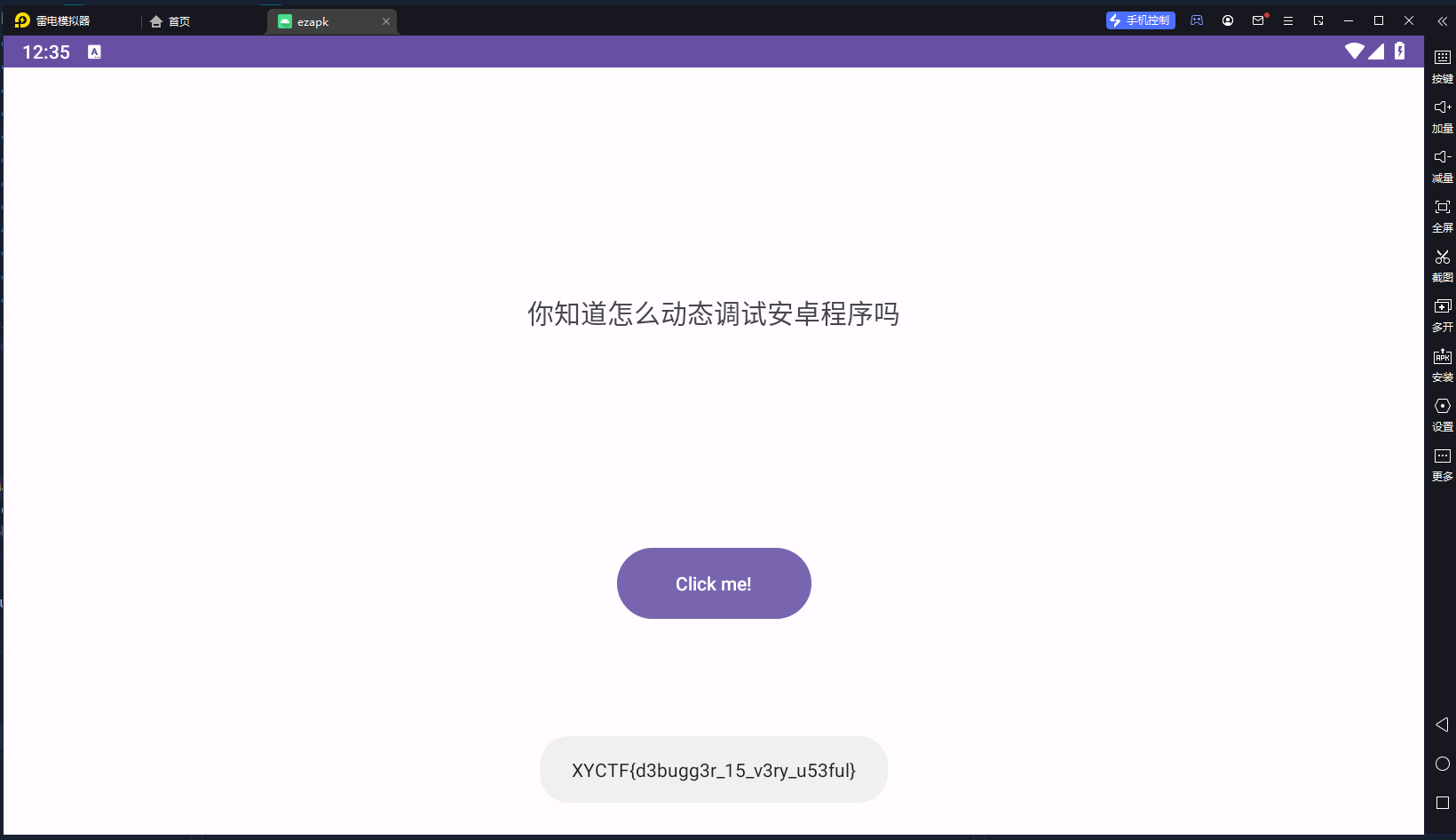
需要debuggable == “true”,但是我没有添加android:debuggable = “true”到mainfest.xml中,只是附加了进程。flag便出了
ez_cube
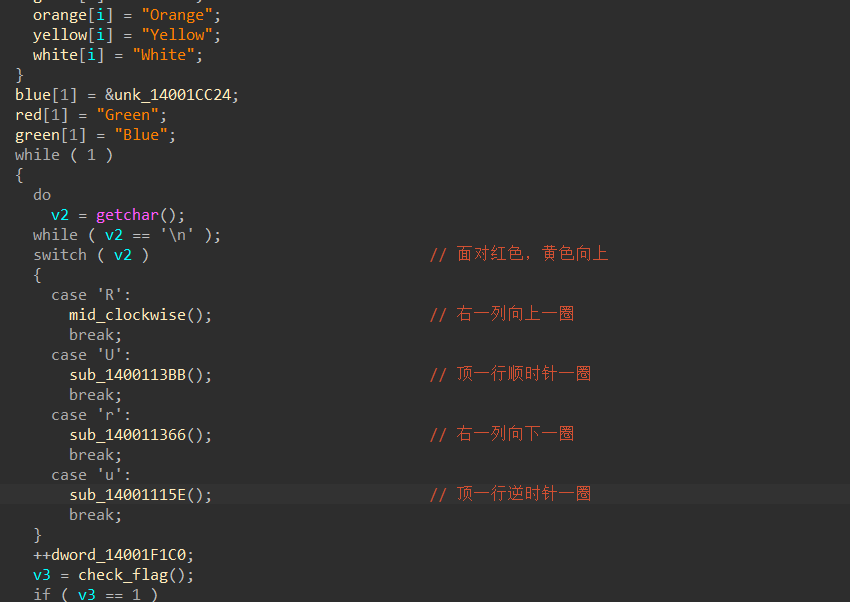
操作分析如上
该魔方的初始化为:
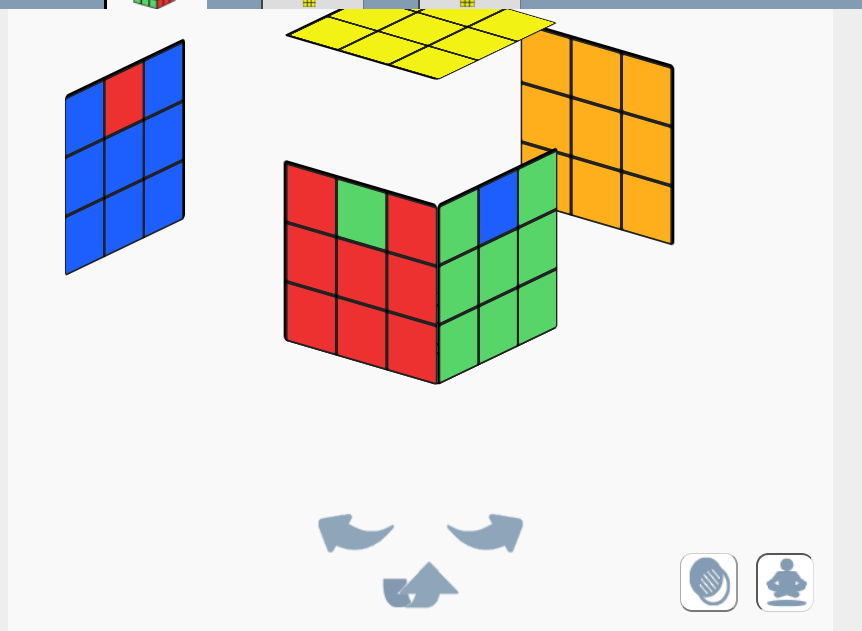
面对红的面,黄色在上,RuRURURuruRR秒了
Trustme
是个apk,jadx反编译:
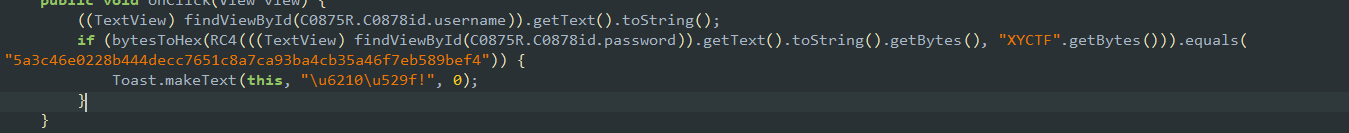
RC4解密一下得到:
The Real username is admin
将admin作为username输入进去,failed,回到jadx发现有个proxyapplication,创建了一个shell.apk,模拟器搜一下,导出来

然后jadx打开,发现是个sql注入漏洞,将username与password作为参数注入,然后查询数据库,数据库是资源文件下assets下的mydb.db,但是在之前创建shell.apk时对数据库文件进行加密,虽然在得到的shell.apk中有解密的代码,但我在模拟器上输入时仍然是failed:
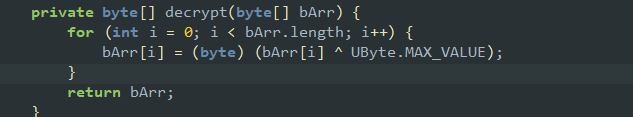
所以手动解密:
1 | with open("C:\\Users\\86158\\Documents\\leidian9\\Pictures\\shell\\assets\\mydb.db", 'rb') as p: |
解密后的的db文件winhex打开可以直接看到flag

什么sql注入,不会
XYCTF{And0r1d_15_V3ryEasy}
ez_rand
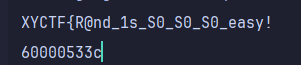
Windows下的C语言随机数生成,种子未知,应该需要爆破,然后看程序头

6开头,爆破到70000…
1 | #include <stdio.h> |
结果:
砸核桃
NSPack壳,吾爱破解脱壳,找到OEP:
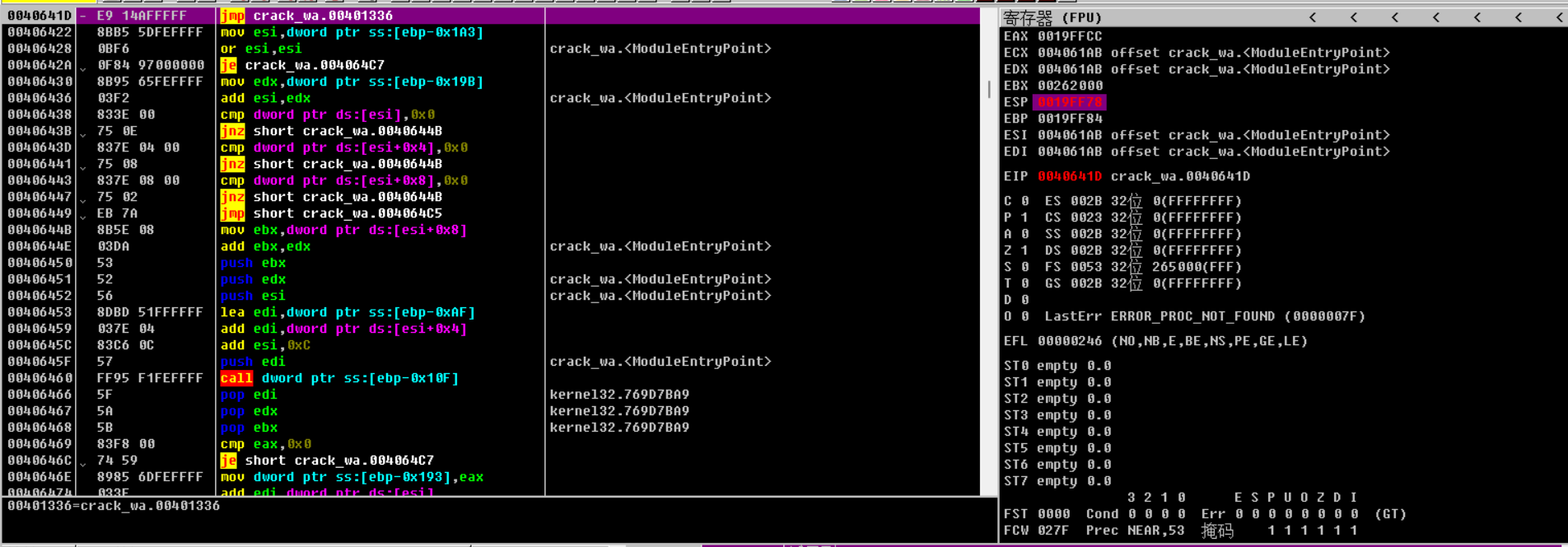
修IAT:
1 | order = 'this_is_not_flag' |
1 | flag{59b8ed8f-af22-11e7-bb4a-3cf862d1ee75} |
ez_math
pyc反编译,得到py代码
本来想用z3解的,写一半发现个规律:)
条件中减去的数都是偶数,并且最后一个元素是减250,125(’}’)的2倍,秒了
1 | table = [88, 89, 67, 84, 70, 123, 113, 55, 87, 89, 71, 115, 99, 85, 117, 112, 116, 84, 89, 88, 106, 110, 106, 75, 111, 121, 85, 84, 75, 116, 71, 125] |
1 | XYCTF{q7WYGscUuptTYXjnjKoyUTKtG} |
what’s this
lua在线反编译,主要逻辑在最后,解密:
1 | cipher = '==AeuFEcwxGPuJ0PBNzbC16ctFnPB5DPzI0bwx6bu9GQ2F1XOR1U' |
1 | U1ROX1F2QG9ubWxwb0IzPD5BPnFtcW1CbzNBP0JuPGxwcEFueA== |
给阿姨倒一杯卡布奇诺
变种tea加密:
- 在正常tea基础上添加了”^ (sum + i)”操作
- 添加了data1和data2对加密时输入的明文进行处理
解密时要注意这两点
解密代码:
1 | #include <cstdio> |

1 | XYCTF{133bffe401d223a02385d90c5f1ca377} |
misc
熊博士
苦思冥想发现是替换密码,以ABCDEFGHIJKLMNOPQRSTUVWXYZ为表,以左右分别有13个字母的位置为对称线,将对应字母替换为对称的字母。
1 | table = 'CBXGU{ORF_BV_NVR_BLF_CRZL_QQ}' |

XYCTFLIUYEMEIYOUXIAOJJ,然后换成小写+flag头、
osint1
洛阳龙门站,搜目的地为泸州的高铁,只有一个车次,再搜洛阳景区,挨个试,运气比较好,第三次出了,河南洛阳老君山
crypto
Sign1n[签到]
1 | from Crypto.Util.number import * |
解密脚本应该是没问题的,不知道为什么得到的结果是错的,而且字节对应的整数除以2就是flag每个字符的ascii