ACECTF 2025 WP by Flooc
ACECTF 2025
reverse
Significance of Reversing
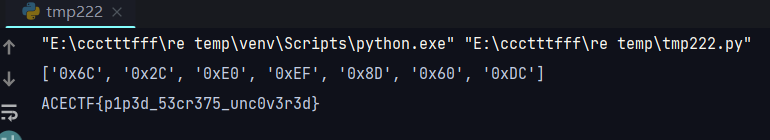
通过winhex观察二进制数据,发现elf文件倒过来了,reverse一下(
然后就是解密
1 | # with open(r"C:\Users\86158\Downloads\Reverseme.png", "rb") as p: |
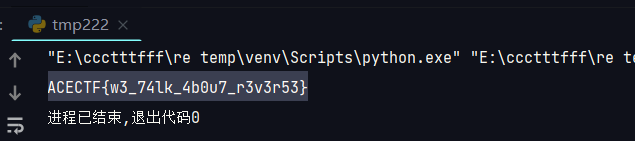
The Chemistry Of Code
简单的rust源码逆向。。
1 | username = "AdminFeroxide" |
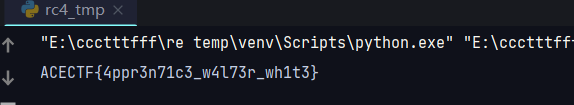
trust item
自定义了一个函数叫strcmp,点进去是注意逻辑。。
1 | cipher = [ |
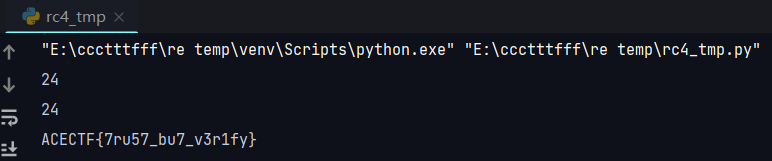
Piped Up
根据输入的数字进行对应的加密操作
对于这几个情况,有writefile和readfile肯定是中间的步骤,只有writefile的是第一个,只有readfile的是最后一个步骤,所以4是第一个,2是最后一个,1,3,5三个加密以某种顺序进行若干次。。
1是流异或,3是与0x56异或,5是与v6进行循环异或,并且flag长度应该为39个字符。
首先是找到加密顺序,我这里使用爆破脚本 ,总共加密次数要手动改:
1 | tab1 = [0x7B, 0x2E, 0xF1, 0xEB, 0x8B, 0x76, 0xE7, 0x68, 0x77, 0xA3, 0xEF, 0x52, 0xF6, 0x3C, 0xDA, 0xAA, 0xF6, 0xA7, |
找到顺序:
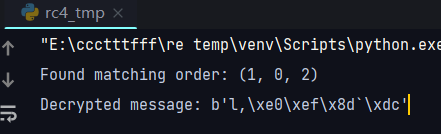
然后就是解密:
1 | tmp1 = [tab1[i] ^ cipher[i] for i in range(len(tab1))] |
DONOTOPEN
一个bash脚本,gzip解压一个py文件,也挺ez的,首先找到gz文件头,1F 8B,然后将之前的字节全删掉,重命名为gz,winrar解压,得到py文件,打开是一个哈希值计算。。
1 | import hashlib |
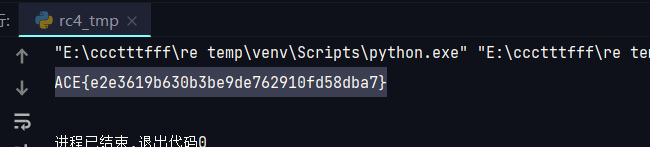
这道题我一开始拿到的附件有问题,gz部分有大量的 EF BF BD这三个字节,题目描述说是又混淆,还以为这是混淆,但又没有gz文件头,感觉有点懵了,后来重新下了个附件是正常的了。。
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Flooc!