flareon11 writeup
flaren-on11_re_by_Flooc
1-frog
1 | cipher = "\xa5\xb7\xbe\xb1\xbd\xbf\xb7\x8d\xa6\xbd\x8d\xe3\xe3\x92\xb4\xbe\xb3\xa0\xb7\xff\xbd\xbc\xfc\xb1\xbd\xbf" |
2-checksum
go逆向,使用xchacha20poly1305加密flag.jpg。
与正常的chacha20poly1305不用的是,x___是扩展版的,key仍是32字节,nonce变成24字节。
逻辑就是先整几个随机数,然后输入他们的和,check一下对不对,最后输入64长度的key,然后将它hex编码。。
先IDA反编译一下,看到这里nonce应该是取自32字节的key的前24字节
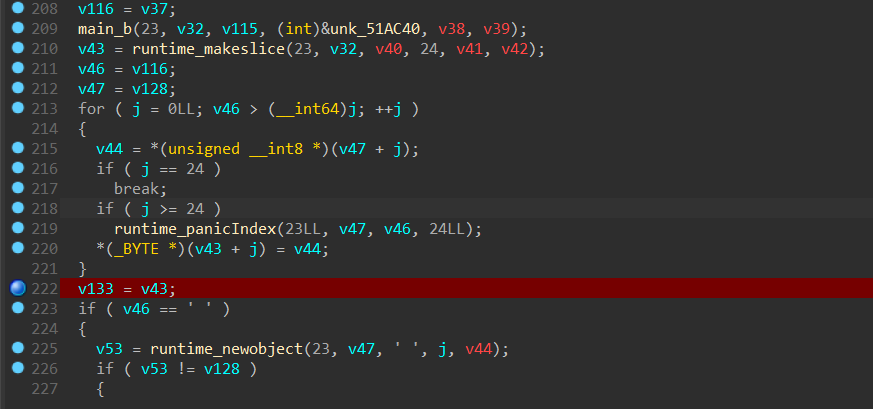
然后就是将key异或后base64,这里IDA动调到的是错的,不知道为什么,可能是我前面nop了不改nop的东西?
有一个main_encryptedFlagData,有0x2c52c的字节的大小,应该就是加密后的flag了,用python脚本拿出来:
1 | import idc |
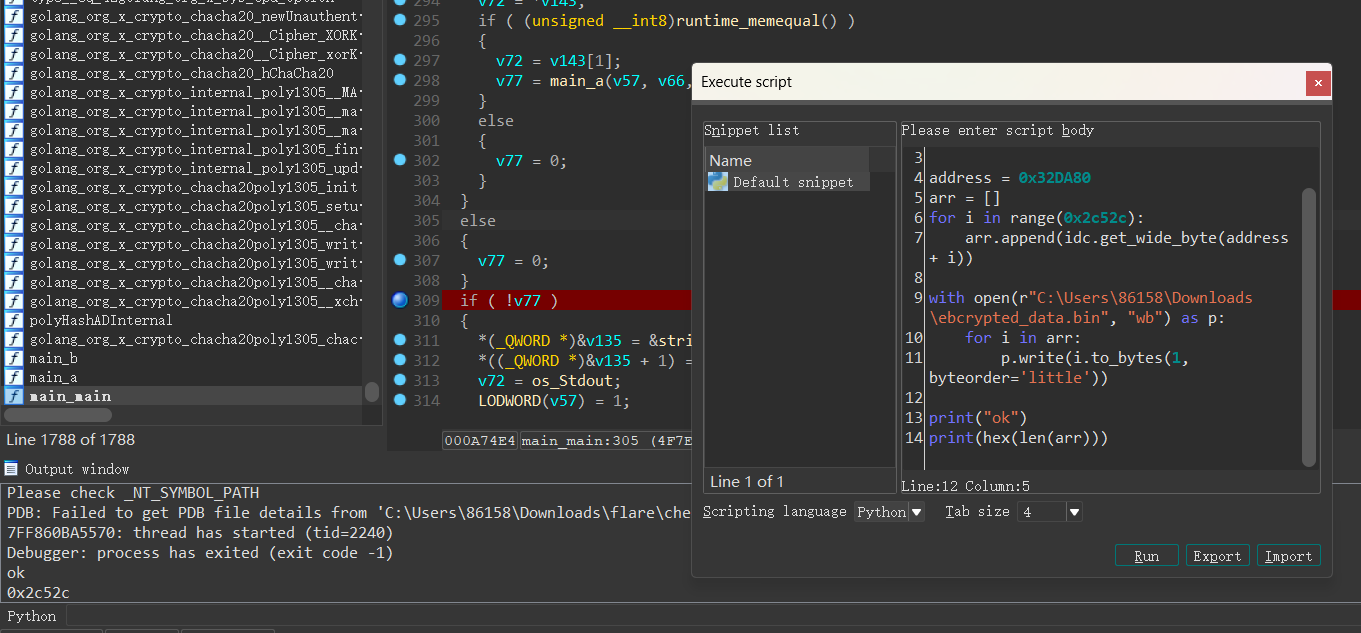
用ghidra和bn看到最后的Base64check的key密文数据
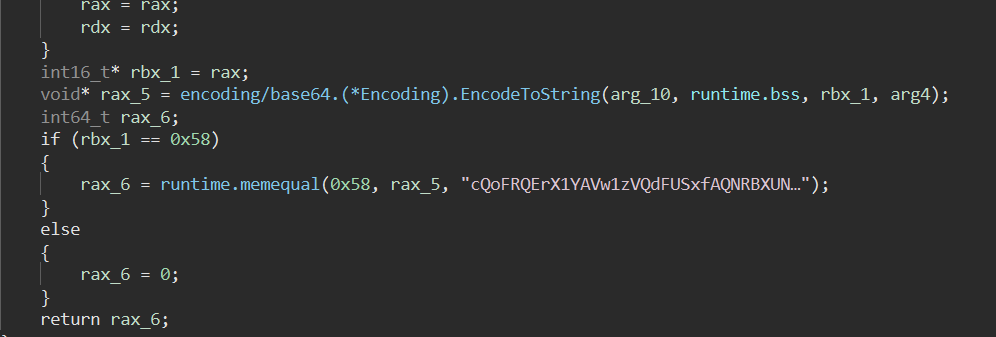 拿出来解密一下得到key:
拿出来解密一下得到key:
1 | import base64 |
最后就是写个go脚本解密这个文件
1 | package main |

3-aray
手搓。。
先提取每个字节相关的condition,与crc32和md5的condition:
1 | import re |
先算hash相关的几个字节,采用爆破,大概模板是一样的:
1 | import hashlib |
剩下的就是可以直接计算结果的,要注意uint32的计算完要反过来赋值,比如uint32(3):
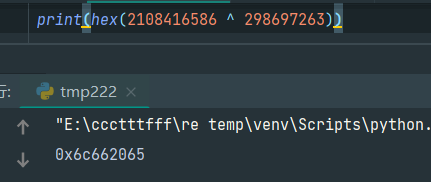
1 | 3 -> 0x65 |
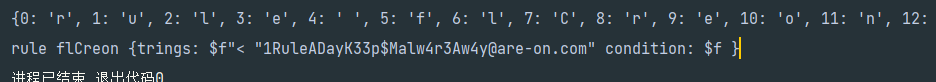
最后搓出来下面这样的,我这里用字典表示。。:
1 | known_data = {0: "r", |
有的位置的字节是需要爆破的,但是看一眼,flag部分的字符是连续的,在最后补上flare-on.com就行了
4-Meme Maker 3000
js混淆,,解混淆一下 https://js-deobfuscator.vercel.app
a0e是图片的base64编码,太多了删掉,逻辑很清晰了
1 | const a0c = ["When you find a buffer overflow in legacy code", "Reverse Engineer", "When you decompile the obfuscated code and it makes perfect sense", "Me after a week of reverse engineering", "When your decompiler crashes", "It's not a bug, it'a a feature", "Security 'Expert'", "AI", "That's great, but can you hack it?", "When your code compiles for the first time", "If it ain't broke, break it", "Reading someone else's code", "EDR", "This is fine", "FLARE On", "It's always DNS", "strings.exe", "Don't click on that.", "When you find the perfect 0-day exploit", "Security through obscurity", "Instant Coffee", "H@x0r", "Malware", "$1,000,000", "IDA Pro", "Security Expert"]; |
remake到有三个输入框的,根据条件,三个输入框内分别是:
1 | b = a0c[14] = "FLARE On" |
输入进去,alert出来了
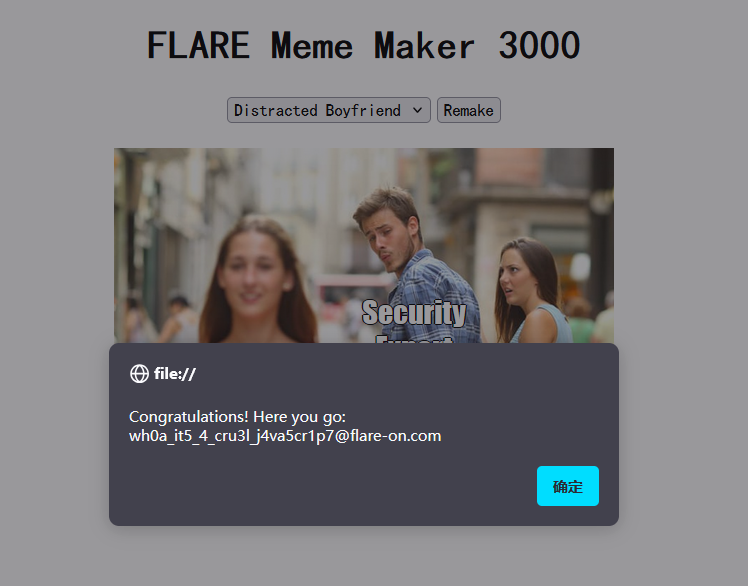
这次只做到这了,第一次做这种题,主要还是对Linux系统和linux系统调试工具不是很熟悉,再加上是第一次做这种很像取证的题目,被硬控了很长时间也没做出来。
网上能搜索到很多大佬的WP,看完后也是有很大感悟。